DNSSEC validation in Microsoft DNS Server 2012
The DNS Server in Windows 2012 now supports all bits and pieces necessary to validate DNSSEC signatures and keys in the Internet (including SHA256 and NSEC3). Here is a small tutorial on how to import the trust anchor for the Internet root zone into the Windows 2012 DNS Server to enable DNSSEC validation:
1. enable DNSSEC validation
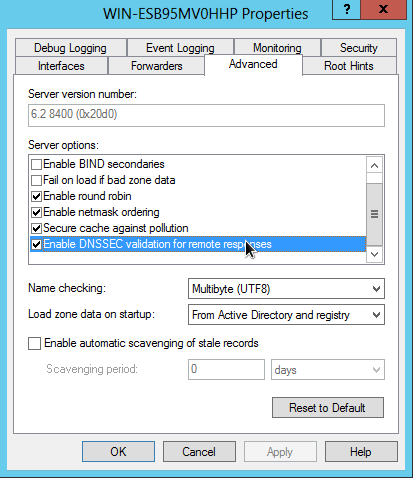
DNSSEC validation can be enabled in the DNS Servers global properties
(Advanced - enable DNSSEC validation for remote responses)
2. import or add the current public DNSKEY for the root zone
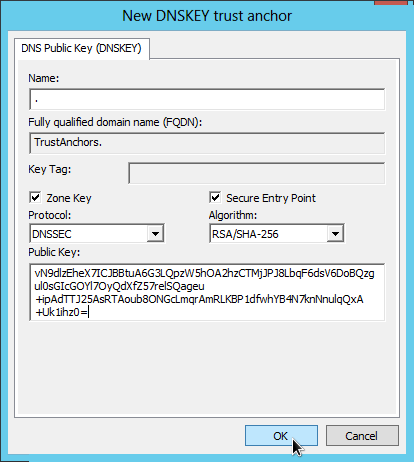
Now we can add the public DNSSEC key (the key signing key, or KSK, flag field value 257) for the root zone as a trust anchor (trust point) into the system (This tutorial uses the root public key that was valid in June 2012). There are two way to enter the trust anchor:
- by importing from a file
- manually adding the key material
Importing the trust anchor from a file
The Windows 2012 DNS Server is picky about the format of the trust
anchor file to be used. It must be in the same format as the keyset
files created by the DNS server when signing a DNS zone. The format is
the same as produced with the BIND 'dig' tool in the versions 9.6 and
9.7 (using the +multi switch), but the Windows 2012 DNS Server will
not take the format produced by 'dig' from BIND 9.9+.
Here is the content of the trust anchor file to be imported:
. 172800 IN DNSKEY 257 3 8 (
AwEAAagAIKlVZrpC6Ia7gEzahOR+9W29euxhJhVVLOyQ
bSEW0O8gcCjFFVQUTf6v58fLjwBd0YI0EzrAcQqBGCzh
/RStIoO8g0NfnfL2MTJRkxoXbfDaUeVPQuYEhg37NZWA
JQ9VnMVDxP/VHL496M/QZxkjf5/Efucp2gaDX6RS6CXp
oY68LsvPVjR0ZSwzz1apAzvN9dlzEheX7ICJBBtuA6G3
LQpzW5hOA2hzCTMjJPJ8LbqF6dsV6DoBQzgul0sGIcGO
Yl7OyQdXfZ57relSQageu+ipAdTTJ25AsRTAoub8ONGc
LmqrAmRLKBP1dfwhYB4N7knNnulqQxA+Uk1ihz0=
) ; key id = 19036
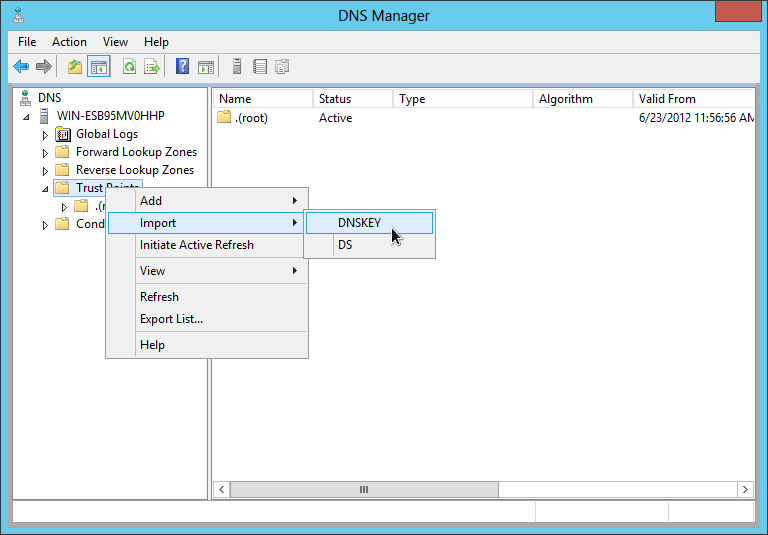
Right click on the 'Trust Points' folder in the Windows 2012 DNS management console and select 'Import - DNSKEY':
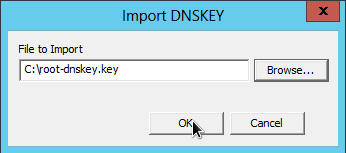
and select the key-file:
Manual adding the key material
Right click on the 'Trust Points' folder in the Windows 2012 DNS Server console, select 'Add - DNSKEY'.
enter "." (dot) as the name for the root zone, and paste the public KSK key (base64 encoded) into the public key field. The DNS server is again very picky about the format of the key material, it must be all in one line without any spaces or line-breaks:
AwEAAagAIKlVZrpC6Ia7gEzahOR+9W29euxhJhVVLOyQbSEW0O8gcCjFFVQUTf6v58fLjwBd0YI0EzrAcQqBGCzh/RStIoO8g0NfnfL2MTJRkxoXbfDaUeVPQuYEhg37NZWAJQ9VnMVDxP/VHL496M/QZxkjf5/Efucp2gaDX6RS6CXpoY68LsvPVjR0ZSwzz1apAzvN9dlzEheX7ICJBBtuA6G3LQpzW5hOA2hzCTMjJPJ8LbqF6dsV6DoBQzgul0sGIcGOYl7OyQdXfZ57relSQageu+ipAdTTJ25AsRTAoub8ONGcLmqrAmRLKBP1dfwhYB4N7knNnulqQxA+Uk1ihz0=
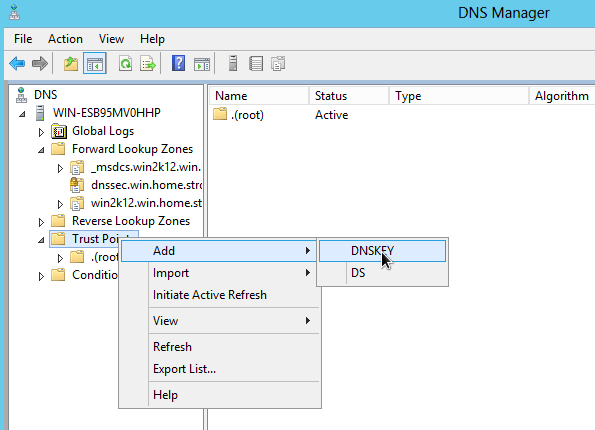
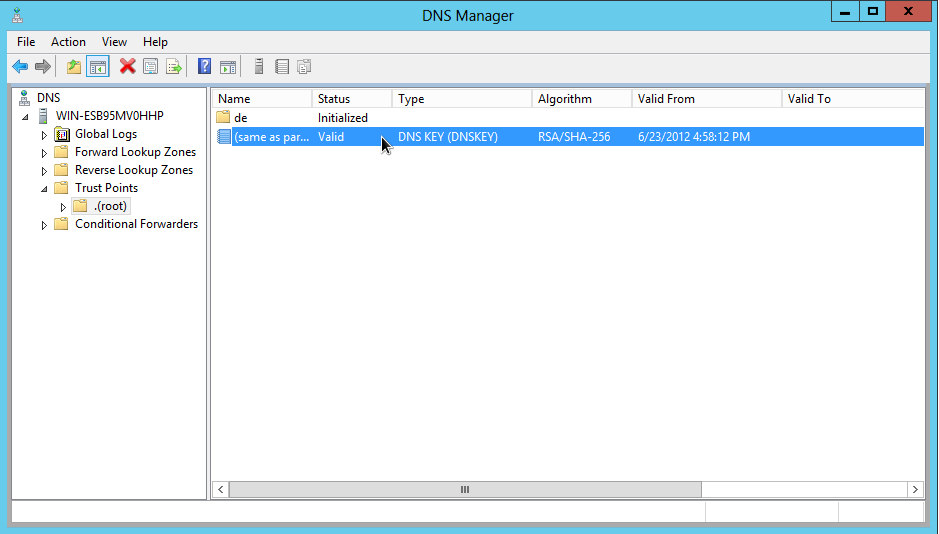
The root zone public key in the trust points folder
The public key of the root zone should now be listed in the 'trust points' folder:
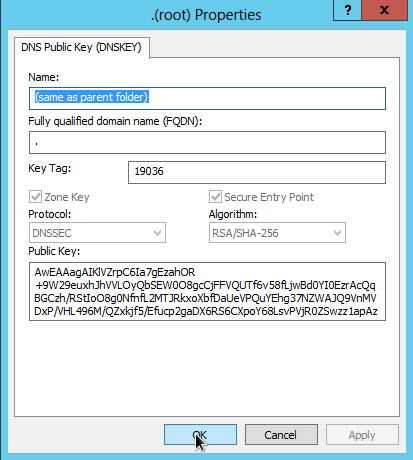
At this point we want to clear the cache of the DNS Server, as the Windows 2012 DNS Server will not validate data that is already stored in its cache.
testing the DNSSEC validation
The PowerShell in Windows 2012 includes a command (resolve-dnsname) to resolve DNS names, including DNSSEC records. However, this command unfortunately does not display the state of the AD (/A/uthenticated /D/ata) Flag in the DNS response header. This AD flag will tell us if DNSSEC validation is working or not.
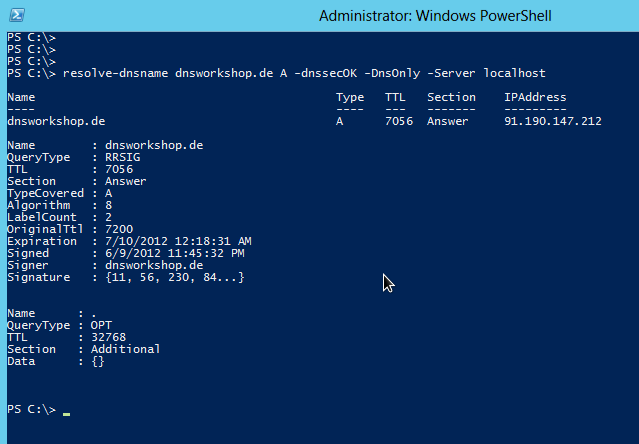
So I downloaded the BIND for Windows distribution from ISC and did a 'tools only' installation, which installs 'dig' (among other tools) on Windows. With 'dig' we can see the AD flag on DNSSEC signed DNS domains, and therefore validate that DNSSEC validation is indeed working for the Windows 2012 DNS Server:
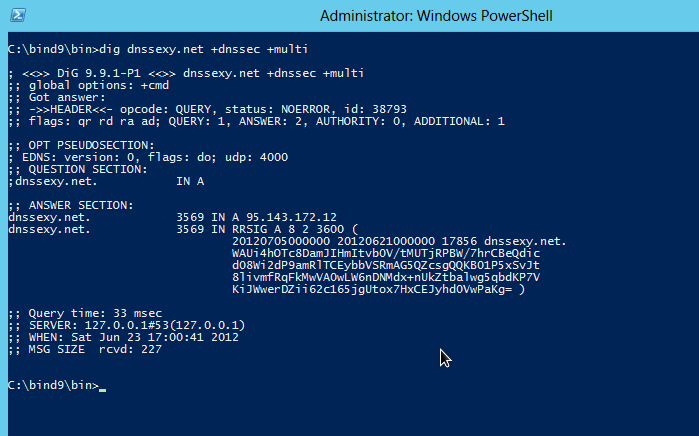
An alternative to installing 'dig' on Windows are websites that offer DNSSEC validation testing.
Update 25 Jun 2012: enabling DNSSEC using 'dnscmd'
as an anonymous reader comments, it is also possible to enable DNSSEC validation from the commandline using the command dnscmd /RetrieveRootTrustAnchors.
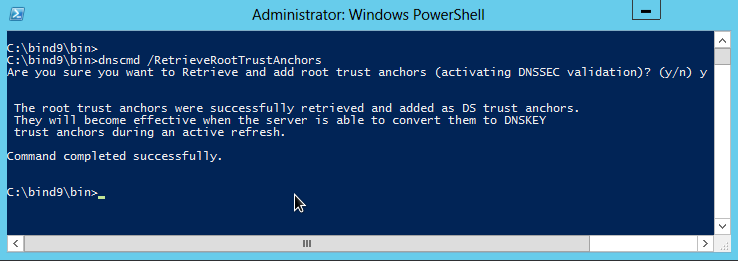
This command will first fetch the delegation signer (DS-record) using https from IANA (https://data.iana.org/root-anchors/root-anchors.xml). The server will then fetch the public key signing key from the root zone during an active refresh cycle (RFC 5011) and validate the KSK using the delegation signer record.
It can take a while until the KSK will appear, and DNSSEC validation can be used. In my tests with Windows 2012 Build 8400 I was not able to trigger an active refresh cycle to speed the process up (but I might have missed something).
